Threat Vulnerability Assessment
A web app that organizes company threats across security domains to increase transparency and efficiency for 60+ active users.
Responsibilities included:
- Sketching
- Wireframing
- Usability Testing
- UX Design
- Design QA
The Problem
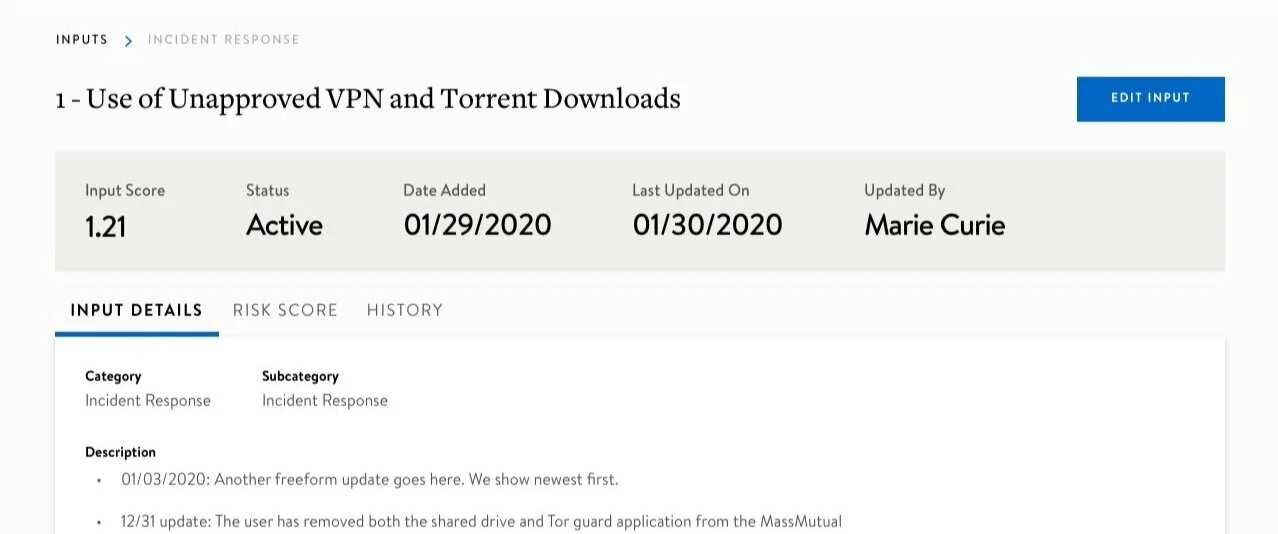
With over 60 analysts updating information prior to a daily call the information was missing, mistakenly overwritten, and unvalidated.
As the security team grew, it became a serious problem when security analysts were all attempting to concurrently edit one Excel sheet with multiple tabs in a shared drive. With over 60 analysts updating information prior to a daily call the information was missing, mistakenly overwritten, and unvalidated. That made daily calls tedious for the facilitator and responsible analyst to clean up the input while on a call and wasting time. Security threats can instantly ruin a company’s reputation, cause low customer confidence in their brand, and cost millions in fees. This product is part of the new security mission to proactively track threats so that they can prioritize their daily focus.
An example of the Excel sheet all security analysts were updating prior to the daily status call.
My goals were to streamline the threat input process, reduce information mistakes, and make the daily call enjoyable for both the facilitator and analyst.
Goals
I attended daily calls to listen and observe how the facilitator and analysts interacted with each other and with the original Excel file. From those observations, as well as speaking with the stakeholder, I synthesized the observations into three major guiding goals.
Goal 1
Streamline the input process
Goal 2
Reduce information mistakes with form hints, validation, and clear language
Goal 3
Focus on features that benefit the facilitator and analyst roles
Concept Validation
Usability testing with 8 users revealed I needed to tackle confusing terminology, loss of context during edit mode, and constant looking around for key information about a threat.
The Reception
On our June 2020 launch we heard feedback from people that “this works amazingly well and is a huge step up from our previous Excel sheets!”
In 5 months we launched an experience that helps analysts input new threats and manage updates while also creating features to help a daily meeting facilitator. There are over 60 active users daily and growing. The project team and I are now working towards minimizing our tech debt, enhancing the edit features, and introduce an administrative tool.
Provides a pulse for the risk level of the company
Key information assists the facilitator during calls
Form feedback and validation reduces persistent data errors
Next Steps
Next steps will be exploring in-line editing, synthesizing major themes across threats, and using natural language processing to determine similar threats.
Users wanted to be able to edit threat updates without losing the context of previous updates. The smoother we make the input process, the more time the team spends on addressing threats.
Mapping threats to major themes over time to help the analysts anticipate risks before they occur. For example if they notice there’s a repeating trend of email scams that target users during the tax refund season, the team knows to sent out preventative tips to our clients beforehand.
Map threats in the tool to other similar threats by analyzing the information and cross-comparing. This will help analysts reach out to other security team members and learn from how the threat was addressed.